iOS Application Security Testing & Pentesting
Introduction:
Apple Inc., the largest consumer electronics manufacturers in the world is popularly known for its unique, innovative design and hardcore security features that it provides to the end consumers. The Apple product lineup uses indigenously developed iOS as the operating system to channelize the communication between hardware and software.
iOS is derived from OSX, with which it shares the Darwin Foundation and is therefore a UNIX like operating system, in nature. It’s the operating system that powers the iPhone, iPad, iPod and Apple TV. Apple designed the iOS platform with security at its core and the application built on and for this platform are very less vulnerable compared to the other competing platforms.
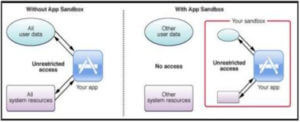
To safeguard the integrity of the customer data and privacy iOS uses Sandboxing method where the different applications are allowed to process their tasks and the data in a particular environment created for them. Let’s understand how it is one in detail-