Managing Cyber-Attacks in a time of Pandemic
TOC
- Background
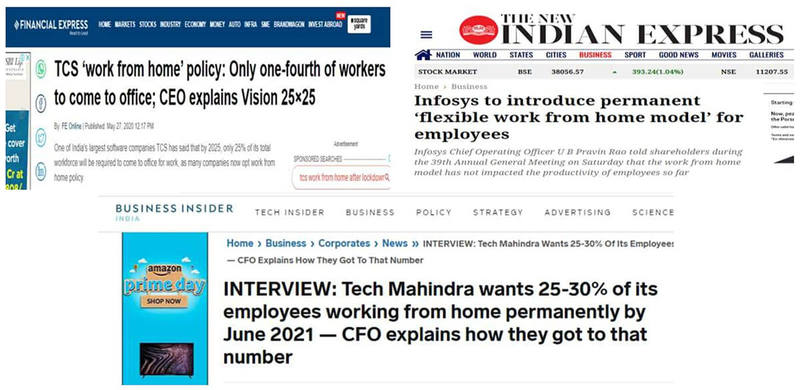
- Work From Home- New Normal
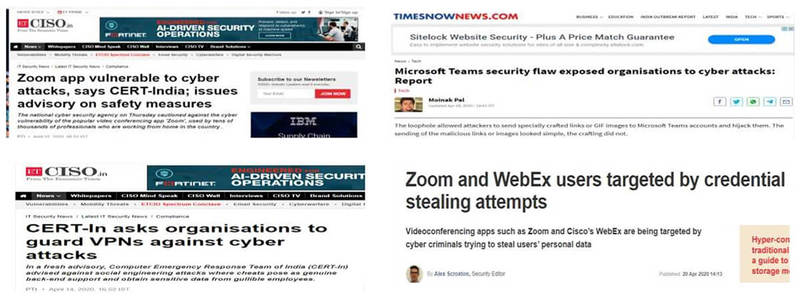
- Increase Cyber Attacks (Recent cases)
- Root Cause
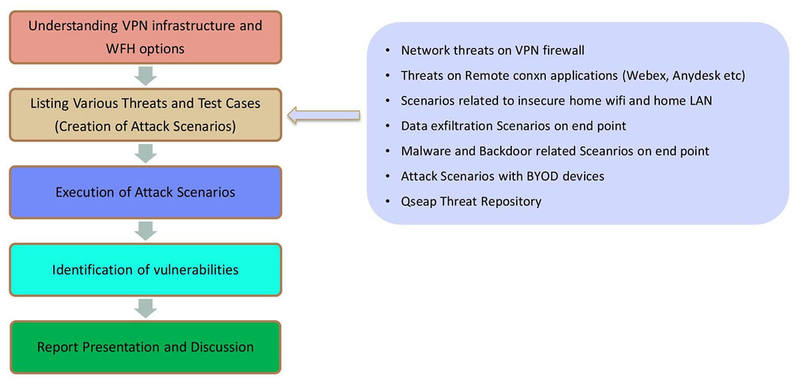
- “Work From Home” Attack Simulation
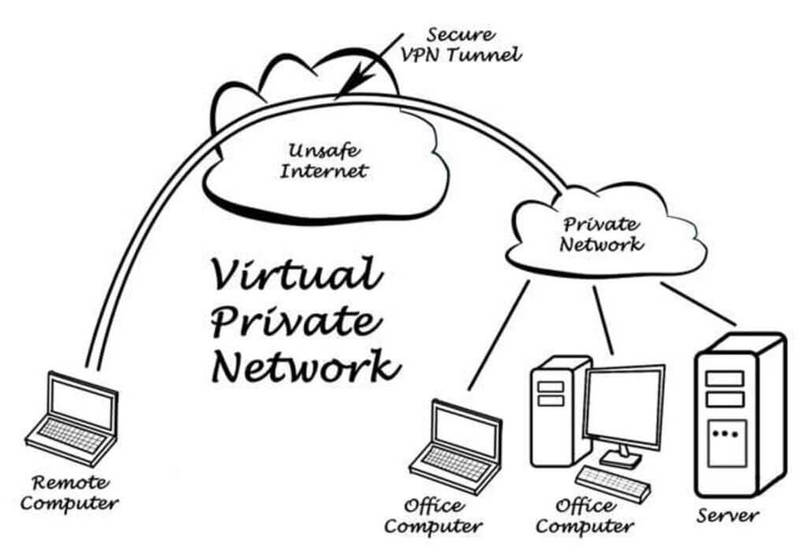
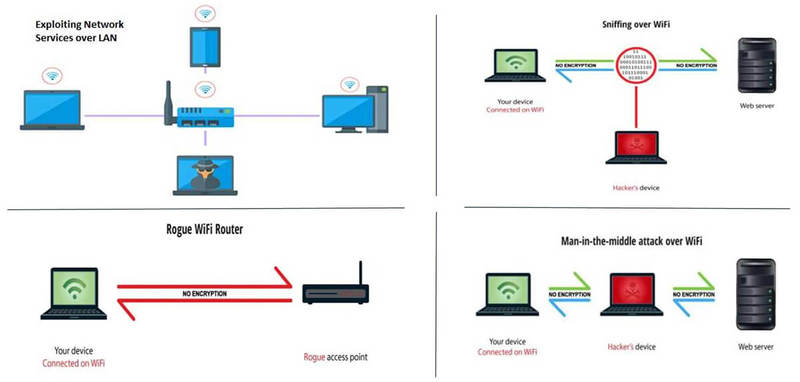
- Threats on VPN Firewalls and Remote Connection Applications
- Threats arising due to WFH (Insecure home WIFI, Data Leakage, Other threats etc)
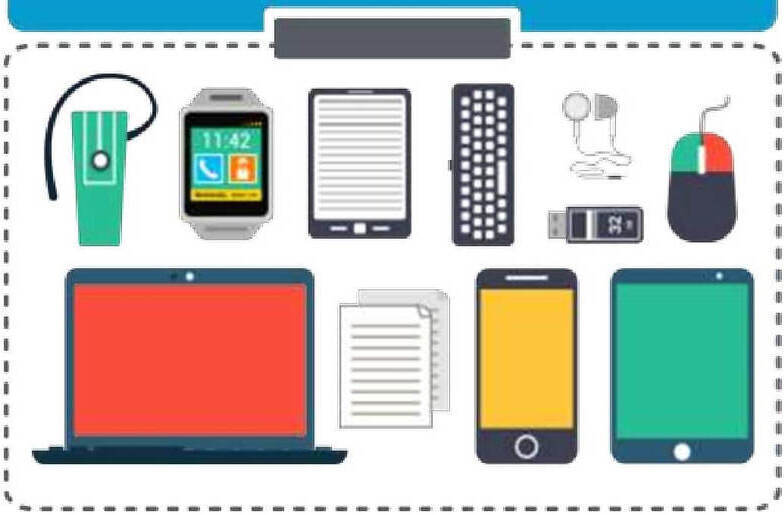
- Threats arising from BYOD devices
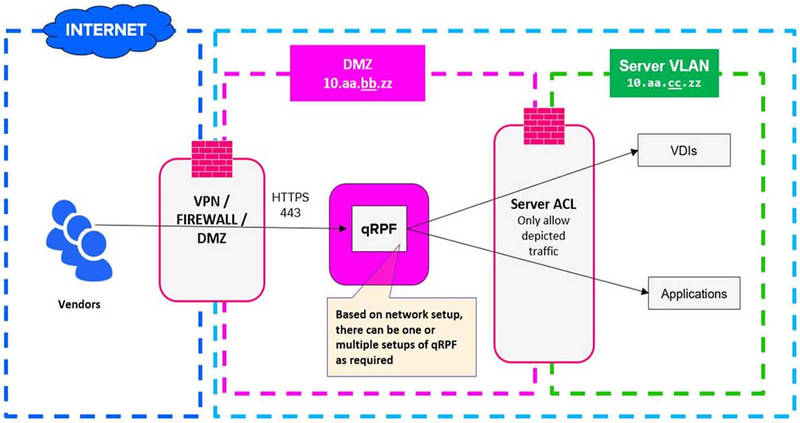
- QRPF (Qseap Remote Pentesting Framework)